Identity Access Management
If you’ve just landed here, we’re doing a “Become a Cloud Architect” Unicorn Workshop by building a Unicorn Pursuit Web App step by step, and you’re more then welcome to join!
About IAM
IAM allows you to manage users/services, and their access to the AWS resources.

IAM is universal, and doesn’t depend on any region or AZ.
Core concepts are:
- Users, who log in to AWS.
- Groups, as collections of users with common set of permissions.
- Role, that defines a Set of Permissions, which can be Assumed by User or AWS Resources. For example, to enable EC2 instance to access S3 bucket, you should Create an IAM role with read-access to S3 and assign the role to the EC2 instance.
- Policy Documents, as a JSON that defines permissions, written as Key Value pairs.
For us, the most important concept is that of a Service Role. Service Role is like a User Role, but it’s assumed by a Service, such as AWS ECS (Elastic Container Service). It’s used to allow our Container (ECS) or Virtual Machine (EC2) to access other AWS Resources.
To configure a Service Role, we need to define:
- Service that would assume a Role. In our case, that will be our ECS Task.
- Set of Policies, that consist of resources (a resource we will be accessing, such as S3), and actions (what we want the resource to be able to execute, such as readBucket or).
Code
To understand what exactly we’re building, refer to the diagram below:
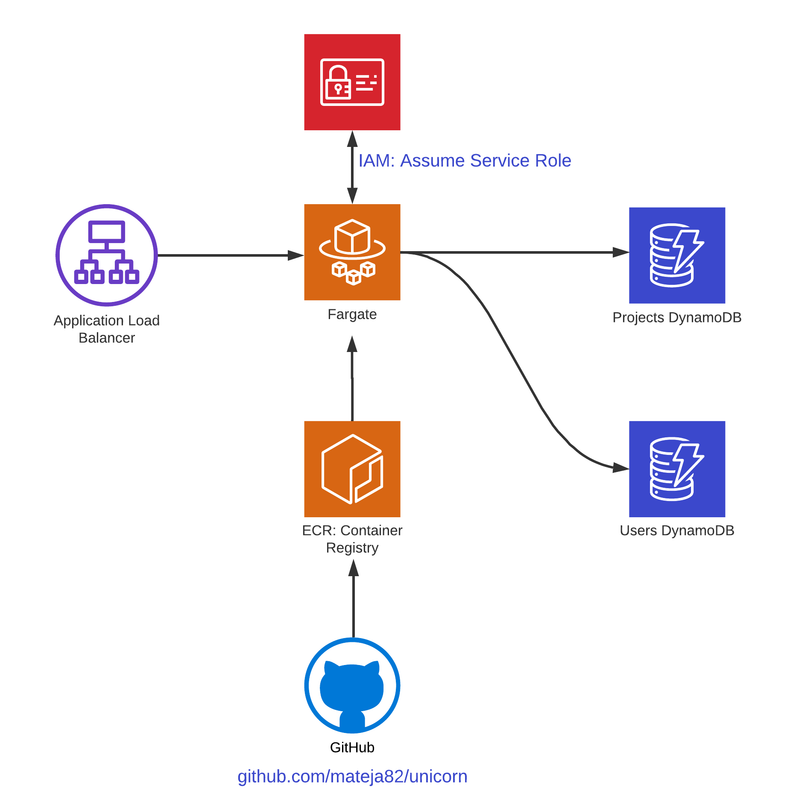
First, we need to import IAM library to our AWS CDK Python file:
from aws_cdk import (
...
aws_iam as iam
)
Don’t forget to install these using pip install aws-cdk.aws-iam and update your requirements.txt, check out this post for details before you can import these to your Python AWS CDK Code.
Create IAM Service Role in AWS CDK
IAM Permissions are split in 3 categories:
- Cluster permissions: who can describe or launch new tasks.
- App Permissions: Allows app containers to access AWS resources.
- Housekeeping Permissions: Allows ECR image pull, ENI creation, CloudWatch logs pushing, etc.
For App Permissions, we first need to create a Service Role called fargate_role, which will be assumed by our ECS Task, and then add Policies per each Service we need, always following the least privilege principle.
fargate_role = iam.Role(
self,
"ecsTaskExecutionRole",
role_name="ecsTaskExecutionRole",
assumed_by=iam.ServicePrincipal("ecs-tasks.amazonaws.com"),
description="Service Role assumed by ECS Fargate (container)"
)
To grant S3 Read/Write from our www.unicornpursuit.com bucket, and our DynamoDB Tables, we need to add the policies. Check out the code below, we’re adding a Policy with Resources: our S3 bucket, and Actions: S3_all.
fargate_role.add_to_policy(statement=iam.PolicyStatement(
resources=[bucket.bucket_arn],
actions=["s3:*"]
))
Feedback
Was this page helpful?
Awesome! Please tell us how we can improve.
Sorry to hear that. Please tell us how we can improve.